Understanding the software bill of materials — or SBOM — is essential to the software product development process. Recently emerging as a key building block in software security and supply chain risk management, the SBOM lists all of the components that make up a codebase and every piece of software used in a product.
You might be wondering: Why does my company need an SBOM? Or maybe you’re concerned about effectively implementing one. We get it — putting together something as technical and complex as an SBOM can be daunting, but doing so can allow your security team to quickly identify any security risks.
Contents
The Software Bill of Materials History
The software bill of materials idea derives from manufacturing, where companies must know where every part comes from — including the company, part number, which factory it’s coming out of and more — to minimize the negative impact of any product defects. Listing all parts built by the original equipment manufacturer and from third-party suppliers helps companies know precisely which products are affected and notify users of the need to update.
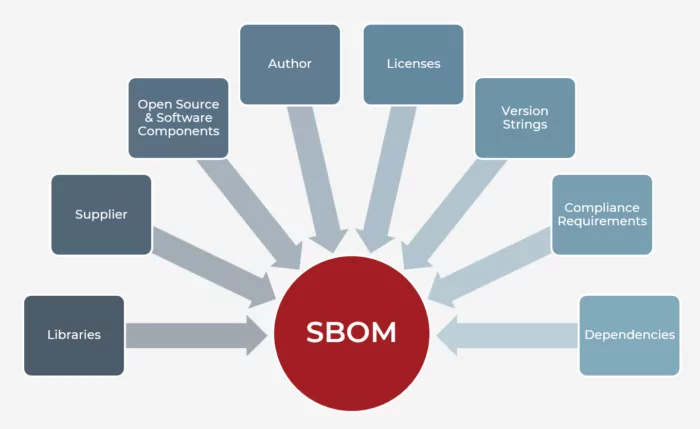
What is a software bill of materials? An SBOM is a list of every piece of software and the exact version used in a product, making monitoring for new common vulnerabilities and exposures (CVEs) that affect your product easier than ever. The purpose of an SBOM is to manage risks in software supply chains by identifying all constituent parts, thus allowing for vulnerability scanning and remediation efforts.
With the 2022 “Open Source Security Risk and Analysis” report revealing 97% of the codebases scanned contained open-source code, failure to adequately secure it can compromise a product’s overall security.
As more layers are added, and languages become more sophisticated, the dependency tree becomes increasingly unwieldy and difficult to track. The software bill of materials came in as an idea to list every package, library, license, every piece of code inside a product — including what it is, who wrote it, what version is running, etc. — to know whether a product is running that package/version and immediately take action. Keeping a list of licenses is important to understand legal requirements when using and changing open-source software.
Software Bill of Materials (SBOM)
Check out this interview on SBOMs: What They Are, What They Are Not, And How Organizations Can Use Them To Makes Us More Secure.
Companies That Need to Implement an SBOM
The digital landscape is fraught with threats, making the implementation of an SBOM paramount for companies dealing with critical infrastructure or sensitive data. High-risk industries, such as health care, energy, aerospace and financial services, are particularly susceptible due to their reliance on intricate software networks, but the OSSRA report highlights the massive potential for open-source risk points within any organization’s digital products.
And implementing a software bill of materials isn’t simply about compliance — it’s good business. Identifying vulnerabilities early on enables quicker response times when issues arise, reducing downtime and maintaining customer trust.
In this era where cyberattacks can simultaneously perpetrate broad attacks across multiple industries, robust defense efforts provide essential insights that help mitigate possible threats before causing significant damage. Creating a complete software bill of materials does require considerable investment, but considering its benefits toward delivering secure products without compromising speed to market makes the effort worthwhile for businesses operating at scale today.
Debunking Common Misconceptions About Your SBOM
Software supply chain risk management is riddled with misconceptions. The most common? Having an SBOM automatically means the product is protected. Wrong!
Once the SBOM is created, someone or some automated process must still monitor the list of CVEs and compare that against the software used.
Another widespread fallacy suggests that an SBOM serves as a treasure map for cyberattackers. This is inaccurate. An SBOM functions more like a flashlight than a roadmap, illuminating third-party components and helping developers pinpoint vulnerable systems within their infrastructure.
Another misconception is emerging in the wake of the executive order issued in July by the U.S. National Telecommunications and Information Administration. Many believe this order mandates all companies to publicize their SBOM, but this directive only applies to vendors supplying software products — including aerospace innovations — to federal agencies. Organizations operating outside this realm retain complete control over their disclosure practices regarding information administration processes.
To clear up these misunderstandings and others surrounding effective software bill of materials implementation, decision-makers should consult reliable resources, such as CISA’s official guide, for accurate insights.
Avoiding Typical Errors When Creating an SBOM
Creating a comprehensive software bill of materials can feel overwhelming, but with understanding and preparation, you can avoid common errors hindering your software risk management efforts.
Let’s explore how to sidestep these potential pitfalls when crafting the SBOM for your next digital product.
Improper Documentation
The most common error organizations make is improper documentation. Incomplete or inaccurate information about a product’s complex web of software components and their dependencies can create a false sense of security. Each field requires precise and comprehensive input; missing details such as version numbers or patch levels might lead to inaccurate vulnerability assessments compromising infrastructure security agency protocols.
During analysis and risk assessment, engineers engrossed in product development often miss important details and vulnerabilities, which can result in breaches. Your approach here needs to be thorough at all costs. Ensuring each data field has accurate inputs will help identify vulnerable systems early on, enhancing overall digital product security.
Mitigating Missing SBOM Information
The first step toward avoiding mistakes is ensuring that no information gets left out. A complete software bill of materials should provide detailed insights about every piece of your product — including third-party and open-source elements. Failing to include any components, license or version information may leave blind spots for vulnerabilities within your system.
Remember this mantra to ensure nothing slips through the cracks: “If it’s part of our software build, it belongs in our SBOM.”
Best Practices for Effectively Implementing a Software Bill of Materials
In software supply chain risk management, a comprehensive SBOM is your first line of defense.
The future trend toward standardizing SBOMs can’t be ignored. Gartner’s 2022 Innovation Insight for SBOMs Report states that companies building or procuring critical infrastructure software will mandate and standardize SBOMs in their software engineering practice by 2025. This forecast underscores why adopting best practices now is essential to delivering secure and reliable software products down the road.
Start With Security
In our interconnected society, software is intricate — and products frequently leverage many third-party components, each harboring inherent vulnerabilities and potential risks. Overlooking the proper security of even a single piece could compromise your entire product. Therefore, building security into every step of the product development process is paramount. By prioritizing security at each juncture of connected product development, the SBOM can be refined to offer comprehensive and accurate insights — ultimately ensuring optimal product security.
Automation
The effectiveness of the SBOM creation process is linked to the level of effort invested in automating dependency discovery within the CI/CD build pipeline. By leveraging automation, building and updating SBOMs is streamlined and simplified, conserving time and effort and minimizing potential errors. Regularly updating your SBOM as new versions or patches roll out ensures you stay on top of any changes in real time. Automated processes increase the likelihood of promptly identifying and addressing issues, resulting in a more efficient approach to generating and maintaining SBOMs.
Define Processes for Creating and Updating SBOMs
Prior to encountering the initial vulnerability, we advise establishing a well-defined strategy rather than formulating one on an ad-hoc basis. Concurrently, assembling a dedicated team to conduct periodic audits is recommended to mitigate the challenges of inadequate SBOM documentation. Continuously refining these processes while addressing vulnerabilities can enhance efficiency and effectiveness over time. Conducting periodic audits to verify accuracy within each data field, from version numbers to origin details, ensures that no key information slips through the cracks when managing open-source and proprietary components.
Alert Key Stakeholders
When communicating with customers and other important parties, whether instructing users to temporarily suspend product usage, providing updates on ongoing resolution efforts, presenting available interim solutions, sharing anticipated timelines for implementing fixes or outlining the severity of the identified issue, do not underestimate the significance of effective communication.
Securing the Future: Elevating Product Security with SBOMs
A critical tool in the digital landscape, SBOMs are crucial for delivering software with enhanced security and integrity. By helping identify vulnerabilities and guide patching efforts, SBOMs help mitigate risks effectively.
As we continue to navigate a digital landscape marked by innovation and connectivity, embracing SBOMs ensures the protection of our creations and bolsters our commitment to delivering secure and reliable solutions to clients worldwide.
Do you need help implementing an SBOM for your next digital innovation? Let our software experts know how we can help!
