Blog Post
Building NFC Readers: Choosing the Right Chip and Implementation Tips
Wondering how to select near-field communication (NFC) readers for your IoT system development? From choosing the right NFC chip to a successful implementation, this third part of our NFC technology blog series, is full of pro tips to get you started.

Blog Post
NFC Reader Design Essentials: Requirements for Tags and Receivers
In the second installment of our series on NFC technology, our engineer shares advice on defining design requirements for NFC readers and requirements for NFC tags and receivers. Learn how the availability of low-cost and extremely useful test gear have made implementation easier.

Blog Post
Counterfeit Protection: Exploring the Role of NFC in the IoT
From enabling secure, tap-and-go transactions to driving innovative IoT applications, NFC is now a ubiquitous force in our lives. But as the threat of counterfeiting and gray market products looms large, learn how NFC technology combats these challenges.
Wondering how to select near-field communication (NFC) readers for your IoT system development? From choosing the right NFC chip to a successful implementation, this third part of our NFC technology blog series, is full of pro tips to get you started.
In the second installment of our series on NFC technology, our engineer shares advice on defining design requirements for NFC readers and requirements for NFC tags and receivers. Learn how the availability of low-cost and extremely useful test gear have made implementation easier.
From enabling secure, tap-and-go transactions to driving innovative IoT applications, NFC is now a ubiquitous force in our lives. But as the threat of counterfeiting and gray market products looms large, learn how NFC technology combats these challenges.
Blog Post
Our Remote Surveillance Camera Innovations Highlighted on Recent Podcast
The future of investigative surveillance is now. Join us as our client Dan Coleman of Creative Solutions Investigative Services discusses rewriting the rules of surveillance technology on the Revenue Fuel podcast.

Blog Post
SBOM (Software Bill of Materials): Strengthening Security through Software Transparency
Learn how an SBOM — or software bill of materials — enhances software security, manages supply chain risks and boosts digital product integrity.

Blog Post
Mobile App Security: Safeguarding User Data and Privacy
Staying ahead of bad actors and protecting your mobile app from vulnerabilities in the ever-evolving threats landscape remains difficult. Learn why mobile app security is important, the most common threats and best practices for enhancing your mobile app development.
The future of investigative surveillance is now. Join us as our client Dan Coleman of Creative Solutions Investigative Services discusses rewriting the rules of surveillance technology on the Revenue Fuel podcast.
Learn how an SBOM — or software bill of materials — enhances software security, manages supply chain risks and boosts digital product integrity.
Staying ahead of bad actors and protecting your mobile app from vulnerabilities in the ever-evolving threats landscape remains difficult. Learn why mobile app security is important, the most common threats and best practices for enhancing your mobile app development.

Blog Post
Top 10 IoT Security Vulnerabilities
Considering the ubiquity of the Internet of Things, IoT security has taken on increased importance in our connected, data-driven world. In this informative blog post, our security expert lays out the top 10 vulnerabilities IoT systems face so that you can remain as protected as possible.

Blog Post
Embedded Security and the Top Properties of a Secure System
With the IoT becoming ever-present in our lives, embedded security has taken on increased importance in a world in which data is a valuable currency. This blog post defines the challenge and highlights the top 10 characteristics of a secure system.

Blog Post
Leveraging IoT Security Standards to Help Ensure Embedded Security
With IoT devices continuing to become ubiquitous, it’s vital that manufacturers, service providers, app developers and retailers understand the many IoT security standards and data privacy laws and regulations impacting the Internet of Things.
Considering the ubiquity of the Internet of Things, IoT security has taken on increased importance in our connected, data-driven world. In this informative blog post, our security expert lays out the top 10 vulnerabilities IoT systems face so that you can remain as protected as possible.
With the IoT becoming ever-present in our lives, embedded security has taken on increased importance in a world in which data is a valuable currency. This blog post defines the challenge and highlights the top 10 characteristics of a secure system.
With IoT devices continuing to become ubiquitous, it’s vital that manufacturers, service providers, app developers and retailers understand the many IoT security standards and data privacy laws and regulations impacting the Internet of Things.
Blog Post
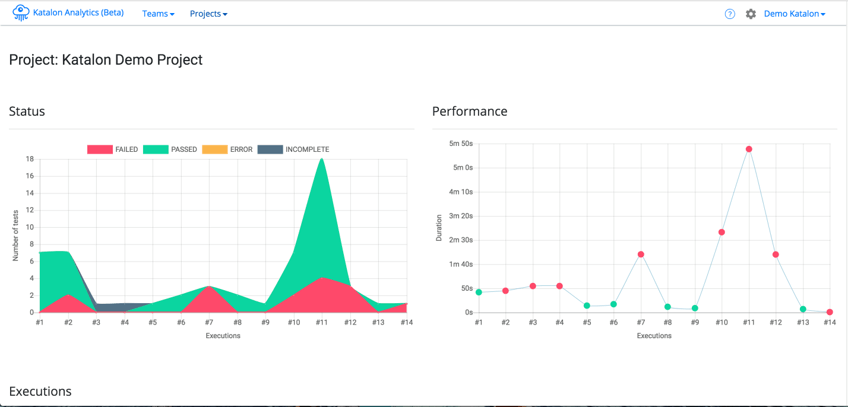
How Katalon Studio Makes Test Automation Easier
Katalon takes the need for learning to program or even the complicated setup of all the tools needed to run a test script and throws it all in a one-stop shop that can be picked up by anyone of any technical skill level in short order to create automation.

Blog Post
Meet Embedded Device Security Webinar Panelist Josh Datko
Josh Datko is the founder of Cryptotronix, co-founder of Keylabs, Inc. and a panelist on our July 15th end-to-end product security webinar. Get to know Josh and register to hear advice for building security into every aspect of an embedded device.

Blog Post
What is the Weakest Link in Your IoT Product Security Chain?
Even the simplest connected device provides a broad range of attack surfaces. Weak security can result in a compromised product, exposed data, downtime and significant damage to a company’s reputation.
Katalon takes the need for learning to program or even the complicated setup of all the tools needed to run a test script and throws it all in a one-stop shop that can be picked up by anyone of any technical skill level in short order to create automation.
Josh Datko is the founder of Cryptotronix, co-founder of Keylabs, Inc. and a panelist on our July 15th end-to-end product security webinar. Get to know Josh and register to hear advice for building security into every aspect of an embedded device.
Even the simplest connected device provides a broad range of attack surfaces. Weak security can result in a compromised product, exposed data, downtime and significant damage to a company’s reputation.
