“A chain is no stronger than its weakest link.”
Think of the security of your IoT product like a chain. While the idiom has a literal meaning, when it comes to IoT product security, the “weakest link” is figurative and usually applies to a technical feature. If just one link in the chain breaks, the entire chain is at risk.
And when even the simplest connected device provides a broad range of attack surfaces, weak security can result in a compromised product, exposed data, downtime and significant damage to a company’s reputation.
Security for IoT devices must consider hardware, software, cloud and app/web interfaces. If potential vulnerabilities are not properly secured across this entire range, you run the risk of getting hacked.
Typical IoT Product Architecture
A common IoT architecture is a system of many elements which may include the device hardware, sensors, protocols, embedded software, manufacturer portals, linked devices and accounts, cloud services, user apps, web interfaces and voice controls. With so much interaction and connection, how do you authenticate every element in a typical IoT device?
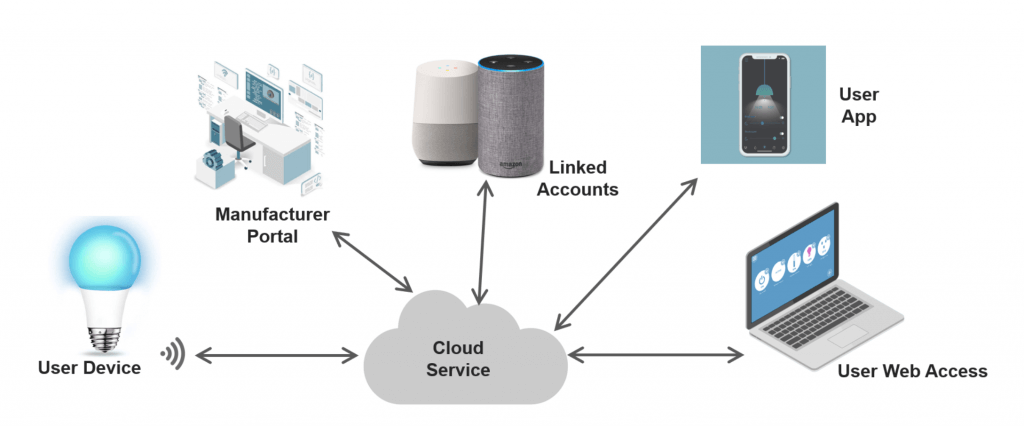
In order to avoid costly and oftentimes dangerous breaches and ensure IoT products are more secure, it’s vital to strengthen security across the entire chain, from architecture through the complete product life cycle.
Contents
Ensuring IoT Product Security throughout the Product Life Cycle
IoT security is about the product’s whole life cycle. It is a story through time. Beyond manufacturing and selling, the product security must be maintained. Consider security at each step – system design, production, operation, etc.
Even if your product has been designed with a hardware root of trust, new vulnerabilities are being found every day. Security needs to continue to be updated as new vulnerabilities are found. A recent high-profile example of this is the Ripple20 vulnerabilities. Cyber security researchers found 19 serious vulnerabilities in a small TCP/IP library at the base of hundreds of millions of IoT products across nearly every consumer facing technology industry. Which of these products is capable of receiving a firmware update? Which companies have systems in place to push the update?
The point is that security is not complete when a product launches. You must design to push updates to devices and build your processes in such a way that your company can get these out in a timely manner.
Integrating IoT Product Security into the Design
Security starts with an appropriate and cost-effective architecture that fits your unique business needs—there is no one-size-fits-all approach that is appropriate for all vendors. During the design and development of connected devices, the engineer looks at what applies to the specific product and designs the overall architecture for product security that considers all the different elements.
Select the IoT Product Security Approach for Your Specific Product
Below are typical things you should consider from an architecture and life cycle viewpoint. This is not a comprehensive checklist for all embedded devices. There are different approaches warranted for the multitude of IoT product types. See what elements apply to your product and as you drill in there are more details to consider.
Not sure where to start? Cardinal Peak has deep expertise in IoT product development to ensure your connected device will be intuitive to set up and use while maintaining security.

Hardware
- Device authentication hardware with secure manufacture
- Tamper evident product design
- Hardware obfuscation
- Debug interfaces disabled in production
- Trust zone
- Electrically isolate life safety systems from network-connected systems
- Electrically isolate crypto assets from rest of system
Embedded Software
- Secure boot
- Automatic OTA updates with security patches
- Minimal open networking ports
- No default usernames/ passwords
- TLS or equivalent encrypted/ authenticated connections; HTTPS if embedded web server
- Secure and authenticated method for firmware delivery
- Automated regression testing for device embedded software
Cloud Service
- Use Transport Layer Security (TLS) for all traffic
- Encrypt sensitive data that is stored in the cloud
- Use revocable access tokens for API authentication (for example OAuth 2)
- Use role-based access control (RBAC) and grant users the minimum set of permissions required
- Store hashed user passwords only, using a random salt and a modern, slow cipher
- For IoT devices, use individual identity certificates that are rotated periodically
- Perform a security audit and penetration test
App/Web Interface
- Consider requiring two-factor authentication
- Do not store credentials locally in the app storage or source code
- For IoT device onboarding, use the cloud as a mutually trusted third party to establish trust between the device and the app
- For IoT devices, carefully consider the security implications of an “offline mode” in which the device and app communicate directly with no cloud
- Test mobile and web app code thoroughly
End-to-End IoT Security Considers Both the Product Design and Long-Term Support
As you can see, hardware, software and connectivity all need to be secure for IoT devices to work effectively. Thus, IoT product security must be an end-to-end consideration, with best security practices considered both at each step of the design and the product life cycle long-term.
Security starts with an appropriate and cost-effective architecture that fits your product’s unique business needs. Because there is no one-size-fits-all approach that is appropriate for all vendors, weakened defense at any entry point puts the entire chain at risk.
Stay tuned for future blogs providing detail and depth on key aspects and challenges of IoT product security.
Register for the End-to-End IoT Product Security Webinar
Join us for End-to-End Security for IoT Product Design, a webinar featuring skilled professionals from Cardinal Peak and two other cybersecurity and engineering companies offering their expert advice, as well as different IoT product security approaches and their trade-offs. The panel discussion will focus on security across the full breadth of a connected device, from hardware through embedded software, radio communication, cloud servers, third-party account access, manufacturer access and end-user control applications. Space is limited — register today!
