While the reports estimating the number of active Internet of Things devices differ, there are undoubtedly billions of IoT devices connecting our world and making it “smarter.” But as the IoT grows, its attack surface does too. Consequently, IoT security has taken on heightened importance in recent years — and it will continue gaining significance as smart “things” become increasingly ubiquitous.
Contents
What is IoT Security?
Despite making our lives more convenient and comfortable, the IoT also opens the door to a broad range of security vulnerabilities. In fact, Kaspersky reported 1.5 billion IoT cyberattacks in just the first six months of 2021, up from 639 million in all of 2020.
Connected devices generate, collect and process a lot of data, and IoT data is highly valuable to bad actors. Complicating the issue, many devices are interconnected, creating a complex web of compromise if just one device gets hacked. Worse yet, many connected devices lack the necessary built-in security controls to defend against threats. As a result, every connected device is a potential target for attack.
Enter IoT security.
IoT security involves, well, securing connected devices — and the networks they’re connected to — from threats both physical and cyber. IoT security also includes a wide range of techniques, strategies, protocols, IoT security standards and actions aimed at protecting, identifying and monitoring risks while helping ameliorate different vulnerabilities.
Since a chain is only as strong as its weakest link, let’s dive into some of the top IoT security vulnerabilities connected devices face so that you can better understand how to prevent hackers from infiltrating IoT devices and protect user privacy.
Top 10 IoT Security Vulnerabilities
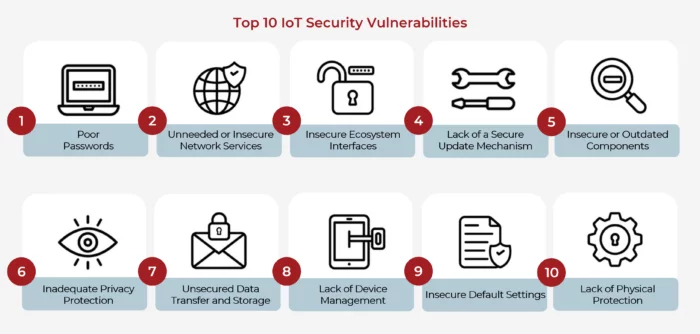
The Open Web Application Security Project (OWASP), an online community that provides free and open security-centric resources, including articles, methodologies, documentation, tools, and technologies, published in 2018 its most up-to-date list of the top 10 IoT security vulnerabilities to avoid when building, deploying or managing IoT systems. While the OWASP list is now several years old, the vulnerabilities remain largely the same today as when the list was initially created.
IoT Security Vulnerability #1: Poor Passwords
Whether weak, unchangeable, easily guessable, publicly available or hardcoded into a device as default, poor passwords are the easiest way for attackers to compromise IoT devices and launch large-scale cyberattacks. In fact, governments around the globe are beginning to ban easy-to-guess default device passwords and require manufacturers to tell users for how long smart devices — including phones — will receive security updates. When designing and developing your IoT product, remember to build security in from the beginning and encourage users to use a new, unique password for every device.
IoT Security Vulnerability #2: Unneeded or Insecure Network Services
IoT devices integrated into networks send and receive data leveraging different communication protocols, from BLE and ZigBee to Wi-Fi, cellular and Ethernet. When a device is connected and communicating, any unneeded or insecure network services running on the device itself can compromise the confidentiality, integrity or availability of information or allow unauthorized remote control. And cybercriminals leverage these unneeded or insecure network services to wreak havoc, whether accessing sensitive information, listening to private communications or executing denial-of-service (DoS) and man-in-the-middle (MITM) attacks, so it’s important to ensure ports not connected to any crucial network services are closed immediately.
IoT Security Vulnerability #3: Insecure Ecosystem Interfaces
From web platforms to backend APIs to cloud or mobile interfaces, any interface outside of the device or its related components can be compromised. With the most common issues including a lack of authentication/authorization, weak or lacking encryption, and a lack of input/ output filtering, too many companies overlook IoT security policies and procedures. A strong authentication and authorization mechanism can help ensure that whenever a server communicates with a connected device, it can differentiate between a valid endpoint and an invalid one by forcing endpoint authentication.
IoT Security Vulnerability #4: Lack of a Secure Update Mechanism
When it comes to IoT device security, the ability to securely update the device’s software and firmware is essential. Unauthorized updates are a major threat vector for IoT device attacks, and organizations across industries often struggle to keep their IoT systems up to date because device manufacturers only provide updated security patches in rare moments. Consequently, connected devices must be able to receive over-the-air (OTA) updates that allow you to “patch” the device’s latest hardware, software and firmware security vulnerabilities over a wireless network.
IoT Security Vulnerability #5: Insecure or Outdated Components
If your device leverages out-of-date or insecure software components, libraries or frameworks, issues can potentially arise from vulnerabilities in software dependencies or legacy systems. Third-party software used to build IoT devices can be difficult to track and is vulnerable to cyberattacks if it’s not correctly managed. Unfortunately, many legacy systems use traditional software update protocols, which force unsuspecting users to find and patch any vulnerabilities. But as today’s cloud-based security infrastructure increases in popularity, it’s important to stay up to date with any firmware or software to ensure your IoT system remains secure.
IoT Security Vulnerability #6: Inadequate Privacy Protection
Given the highly valuable nature of a user’s sensitive personal information, privacy protection is essential in our connected world. Many connected devices collect personal data that needs to be securely stored and processed to remain compliant with various privacy regulations, including Europe’s General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). However, with the Cost of a Data Breach Report 2021 revealing that 44% of data leaks contain personally identifiable information, it’s apparent that a lack of privacy protection will put users’ private information at risk and, even worse, could result in harsh legal consequences.
IoT Security Vulnerability #7: Unsecured Data Transfer and Storage
As mentioned several times, some IoT data is tremendously valuable to bad actors. When sensitive data is not encrypted or lacks access control anywhere within the ecosystem, whether at rest, in transit or being processed, it can be stolen and used for nefarious purposes. Since this data is often used in automated decision-making and to control devices, it is critical that it remains protected as information is transferred across the network or stored in a new location. Consequently, IoT data transfer and storage best practices call for robust private and public encryption keys.
IoT Security Vulnerability #8: Lack of Device Management
When it comes to the IoT, a significant challenge is managing all of the disparate devices and securing the network perimeter. Occasionally, a rogue or malicious device is installed without authorization to collect or alter sensitive information. As is the case with all IT asset management, key IoT device management concerns include the provisioning, operation and updating of all devices and gateways. Traditional IoT device identification using IP addresses and underlying operating systems doesn’t work for the IoT. Instead, you need to identify specific devices to plan network access requirements, deployment tactics, security strategy optimization and operational plans. Once device identities are determined, security systems can track device behavior to recognize malicious communication patterns before they cause damage.
IoT Security Vulnerability #9: Insecure Default Settings
Similar to default passwords, default device settings can be problematic. By restricting operators from modifying configurations or launching connected products with insecure default settings, IoT device makers open the door for compromise. Once an attacker breaches the system, they can exploit vulnerabilities in the device firmware or find hidden backdoors. Recognizing these difficult-to-alter default settings and the security gaps they introduce is vital in implementing the appropriate controls for better securing these devices.
IoT Security Vulnerability #10: Lack of Physical Protection
Unfortunately, many IoT devices are often vulnerable to attack because they lack the necessary built-in security to counter threats. Without physical security measures, attackers have the ability to access sensitive information that can help in a future remote attack or take local control of the device. Since connected devices are deployed in dispersed and remote environments, attackers capable of gaining access to and tampering with the physical layer can disrupt the device’s service delivery. While security protocols protect data in transit, data stored on the device itself remains unprotected, so making sure hardware is safe from tampering, physical access, manipulation and sabotage is imperative.
Learn why mobile app security is important, the most common threats and best practices for enhancing your mobile app development in our blog post Mobile App Security: Safeguarding User Data and Privacy.
Conclusion
Despite the incredible value the IoT delivers to consumers and businesses alike, poor security practices can result in disastrous consequences that do significantly more harm than good. With the Internet of Things becoming increasingly ubiquitous, remaining aware of the primary IoT security vulnerabilities can help ensure your devices and networks don’t fall prey to a damaging cyberattack.
As experts in end-to-end IoT security, we recognize it’s impossible to secure your device, network and IoT system against every imaginable attack. However, by staying up to date with the top vulnerabilities, we can help prevent attackers from compromising your system. If you still need help gaining a better understanding of the most critical IoT vulnerabilities or require our embedded security expertise to better protect your IoT system, let our security experts know how we can help confirm that no holes have been left in your security architecture.
