
Blog Post
Artificial Intelligence
Navigating the Unseen: Preparing for a Non-Linear Future
In a business world facing an unprecedented level of uncertainty, traditional strategic planning is no thing of the past. To stay ahead, leaders need to broaden their focus and proactively engage with a new class of disruptors, from AI's insatiable power demands to the rise of a new global innovation. Read the full blog post to explore the key takeaways from the IBCircle CEO & CFO Global Roundup and discover how to design for disruption.

Blog Post
UX Design
The Top 5 Usability Issues We Find in Most UX Audits (And How to Fix Them)
While every product is unique, our UX audits reveal that most suffer from a handful of common usability issues. This post uncovers the top 5 problems we consistently find, from confusing navigation to inconsistent design, and provides the first steps toward a more user-friendly experience.
Blog Post
UX Design
Inside Our Toolkit: The Power of a Heuristic Evaluation
How does an expert UX audit uncover so many critical issues? It's not guesswork; it's a methodical process. This post pulls back the curtain on a core component of our toolkit: the heuristic evaluation. Learn what usability heuristics are and how we use this powerful framework to diagnose your product’s health.
In a business world facing an unprecedented level of uncertainty, traditional strategic planning is no thing of the past. To stay ahead, leaders need to broaden their focus and proactively engage with a new class of disruptors, from AI's insatiable power demands to the rise of a new global innovation. Read the full blog post to explore the key takeaways from the IBCircle CEO & CFO Global Roundup and discover how to design for disruption.
While every product is unique, our UX audits reveal that most suffer from a handful of common usability issues. This post uncovers the top 5 problems we consistently find, from confusing navigation to inconsistent design, and provides the first steps toward a more user-friendly experience.
How does an expert UX audit uncover so many critical issues? It's not guesswork; it's a methodical process. This post pulls back the curtain on a core component of our toolkit: the heuristic evaluation. Learn what usability heuristics are and how we use this powerful framework to diagnose your product’s health.

Blog Post
UX Design
From Insight to Impact: How to Turn User Research into a Prioritized Product Roadmap
User research can produce a mountain of data, but how do you turn those findings into real product improvements? This post provides a four-step framework for translating raw user insights into a strategic, prioritized product roadmap. Learn how to ensure your research investment leads to tangible business impact.
Blog Post
UX Design
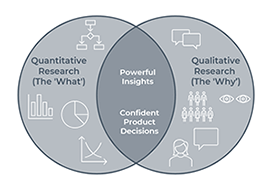
The ‘What’ vs. the ‘Why’: Blending Quantitative and Qualitative User Research
To build a great product, you need to know what users are doing and why. This post breaks down the two types of user research that provide these answers: quantitative (the 'what') and qualitative (the 'why'). Learn the key differences and how blending them provides a complete picture.

Blog Post
UX Design
Moderated vs. Unmoderated: Choosing the Right Usability Test for Your Product
Not all usability testing is the same. The method you choose dramatically impacts the insights you receive. This post breaks down the two primary approaches: moderated and unmoderated. Learn the key differences, the pros and cons of each, and how to decide which method is the right fit.
User research can produce a mountain of data, but how do you turn those findings into real product improvements? This post provides a four-step framework for translating raw user insights into a strategic, prioritized product roadmap. Learn how to ensure your research investment leads to tangible business impact.
To build a great product, you need to know what users are doing and why. This post breaks down the two types of user research that provide these answers: quantitative (the 'what') and qualitative (the 'why'). Learn the key differences and how blending them provides a complete picture.
Not all usability testing is the same. The method you choose dramatically impacts the insights you receive. This post breaks down the two primary approaches: moderated and unmoderated. Learn the key differences, the pros and cons of each, and how to decide which method is the right fit.

Blog Post
UX Design
When is the Right Time for Usability Testing? (Hint: It’s Earlier Than You Think)
Many teams treat usability testing as a final check before launch, but by then, fixing foundational flaws is incredibly expensive. This post makes the case for a modern, agile approach. Discover the right time to conduct user testing throughout the product lifecycle to mitigate risk and save money.

Blog Post
UX Design
Beyond Talent: The Tools and Technologies That Power Our UI Design Process
A great design team is essential, but their talent is amplified by the tools they master. This post takes you 'under the hood' of our UI design process. Discover the technologies we use for precision design in Figma, in-depth user research, and even harnessing AI to create stunning visuals.

Blog Post
UX Design
What is a UX Audit? A Guide to Improving Your Existing Product
Is your existing digital product struggling with low adoption or poor performance? A UX audit is the first step to turning it around. This post explains our expert evaluation process, which assesses your product’s usability and design to identify critical issues. Learn how we deliver clear insights and a prioritized action plan for improvement.
Many teams treat usability testing as a final check before launch, but by then, fixing foundational flaws is incredibly expensive. This post makes the case for a modern, agile approach. Discover the right time to conduct user testing throughout the product lifecycle to mitigate risk and save money.
A great design team is essential, but their talent is amplified by the tools they master. This post takes you 'under the hood' of our UI design process. Discover the technologies we use for precision design in Figma, in-depth user research, and even harnessing AI to create stunning visuals.
Is your existing digital product struggling with low adoption or poor performance? A UX audit is the first step to turning it around. This post explains our expert evaluation process, which assesses your product’s usability and design to identify critical issues. Learn how we deliver clear insights and a prioritized action plan for improvement.

Blog Post
UX Design
What Makes a Great Facilitator? The Core Qualities for Workshop Success
What's the difference between a rambling meeting and a productive Design Workshop? The facilitator. This post explores the essential qualities that lead to a successful session. We'll look at the core values, service mindset, and technical abilities we rigorously hire for.

Blog Post
UX Design
Expert UX Workshop Facilitation: Why a Certified Team Makes the Difference
Not all design workshops are created equal. The outcome depends on the facilitator’s expertise. This post explores how a large, certified team provides a superior experience. Learn how our investment in continuous improvement and certifications in Scrum and Design Thinking leads to a more structured, productive, and valuable engagement.
Blog Post
Connected Devices and IoT
Building NFC Readers: Choosing the Right Chip and Implementation Tips
Wondering how to select near-field communication (NFC) readers for your IoT system development? From choosing the right NFC chip to a successful implementation, this third part of our NFC technology blog series, is full of pro tips to get you started.
What's the difference between a rambling meeting and a productive Design Workshop? The facilitator. This post explores the essential qualities that lead to a successful session. We'll look at the core values, service mindset, and technical abilities we rigorously hire for.
Not all design workshops are created equal. The outcome depends on the facilitator’s expertise. This post explores how a large, certified team provides a superior experience. Learn how our investment in continuous improvement and certifications in Scrum and Design Thinking leads to a more structured, productive, and valuable engagement.
Wondering how to select near-field communication (NFC) readers for your IoT system development? From choosing the right NFC chip to a successful implementation, this third part of our NFC technology blog series, is full of pro tips to get you started.
