Blog Post
Streaming Media From Small Screen to Big Time: Scaling Your Streaming Media App for Success
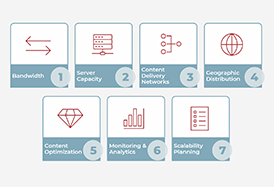
Without proper scaling of streaming media apps, users may suffer through slow or interrupted playback — resulting in a subpar user experience, lost revenue and missed growth opportunities.

Blog Post
Cloud Transformation Cloud Application Observability: Comparing 3 Cloud Monitoring Tools
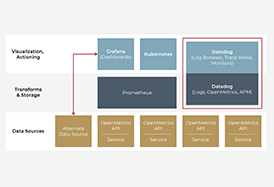
The second post in our cloud application observability series compares different cloud monitoring tools to help readers determine the correct choice for their cloud project. This article focuses on three particular packages: Datadog, Prometheus and Grafana.
Blog Post
Cloud Transformation A Guide to Application Observability with Metrics & Cloud Monitoring Tools
Our engineer shares the capabilities and data flows of common off-the-shelf cloud metrics and cloud monitoring tools - exploring the best way to implement raw data from an app’s services into meaningful dashboards and alerts.
Without proper scaling of streaming media apps, users may suffer through slow or interrupted playback — resulting in a subpar user experience, lost revenue and missed growth opportunities.
The second post in our cloud application observability series compares different cloud monitoring tools to help readers determine the correct choice for their cloud project. This article focuses on three particular packages: Datadog, Prometheus and Grafana.
Our engineer shares the capabilities and data flows of common off-the-shelf cloud metrics and cloud monitoring tools - exploring the best way to implement raw data from an app’s services into meaningful dashboards and alerts.
Blog Post
Streaming Media Understanding Streaming Protocols: How to Choose the Right One for Your Needs
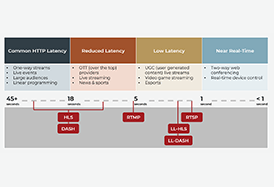
Looking to stream your content but not sure which protocol is the right fit for your project? This blog breaks down the differences between low-latency streaming media protocols and HTTP-based adaptive streaming protocols, discusses the advantages of each and empowers you to make an informed decision.

Blog Post
Streaming Media WebRTC Tutorial for Interactive Video Streaming
WebRTC provides an efficient way to share video, audio and other data without the need for any plug-ins or additional software. Discover how WebRTC enables real-time communication, providing the ability to create dynamic and interactive video experiences.
Blog Post
Audio Streaming Media & Video Encoding Formats and Trade-Offs
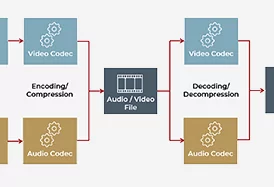
This informative blog post delves into streaming media encoding, different encoding formats and codecs and how they are used to package media for streaming.
Looking to stream your content but not sure which protocol is the right fit for your project? This blog breaks down the differences between low-latency streaming media protocols and HTTP-based adaptive streaming protocols, discusses the advantages of each and empowers you to make an informed decision.
WebRTC provides an efficient way to share video, audio and other data without the need for any plug-ins or additional software. Discover how WebRTC enables real-time communication, providing the ability to create dynamic and interactive video experiences.
This informative blog post delves into streaming media encoding, different encoding formats and codecs and how they are used to package media for streaming.

Blog Post
Cloud Transformation What is the Best Message Queue for Your Application?
From evaluating key metrics and modeling everything upfront to using the most important features as a filter to narrow down your choices, our expert delves into the best practices to follow when selecting the best message queue for your application in the final post of this blog series.

Blog Post
Cloud Transformation Understanding the Cost Drivers Impacting Queue Pricing
In the penultimate post of this blog series, we discuss the most critical queuing service cost drivers, highlighting the importance of understanding how each element will ultimately impact your bottom line.

Blog Post
Cloud Transformation Selecting the Best Queue Data Structure for Your Use Case
In this second part of this blog series, we'll delve into different use cases for queues, highlighting some of the most common computing applications in which queues are utilized.
From evaluating key metrics and modeling everything upfront to using the most important features as a filter to narrow down your choices, our expert delves into the best practices to follow when selecting the best message queue for your application in the final post of this blog series.
In the penultimate post of this blog series, we discuss the most critical queuing service cost drivers, highlighting the importance of understanding how each element will ultimately impact your bottom line.
In this second part of this blog series, we'll delve into different use cases for queues, highlighting some of the most common computing applications in which queues are utilized.
Blog Post
Cloud Transformation Choosing a Queuing Service — Part I
From what a queue is to different types of queues, our engineering expert details why choosing a queue requires careful consideration in part one of this blog series.

Blog Post
AWS From an Irrational Fear of Basement Flooding to an Ongoing Amazon Web Services IoT Class
What began as a project rooted in paranoia that my basement would flood evolved first into a lunch-and-learn I hosted for Cardinal Peak employees. During my initial presentation, I focused on Amazon Web Services' "internet of things" (AWS IoT) services and how I created "SumPy," an AWS IoT-driven sump pump monitor and alert system.

Blog Post
Connected Devices and IoT Some Predictions About the IoT in 2015
I generally am not a fan of the lists-of-predictions articles that tend to come out at the beginning of a year, but when I was approached by SiliconANGLE to make some predictions about the Internet of Things in 2015, I couldn’t resist: In 2015, we will see the proliferation of frameworks for communicating with and... View Article
From what a queue is to different types of queues, our engineering expert details why choosing a queue requires careful consideration in part one of this blog series.
What began as a project rooted in paranoia that my basement would flood evolved first into a lunch-and-learn I hosted for Cardinal Peak employees. During my initial presentation, I focused on Amazon Web Services' "internet of things" (AWS IoT) services and how I created "SumPy," an AWS IoT-driven sump pump monitor and alert system.
I generally am not a fan of the lists-of-predictions articles that tend to come out at the beginning of a year, but when I was approached by SiliconANGLE to make some predictions about the Internet of Things in 2015, I couldn’t resist: In 2015, we will see the proliferation of frameworks for communicating with and... View Article
