Despite its many advantages, Bluetooth LE can present security challenges. In this article, our engineer details what the security concerns are and how to secure BLE devices using randomized addresses.
Contents
What is Bluetooth Low Energy and What are the Advantages?
The Bluetooth Low Energy (Bluetooth LE or BLE) communication protocol was introduced in the 2010s as a lower power consumption alternative to the original Bluetooth Basic Rate/Enhanced Data Rate (BR/EDR) protocol (also called classic Bluetooth). Bluetooth LE devices achieve lower power levels than classic Bluetooth by enabling faster connections and shorter connection intervals, resulting in more low-energy standby time. Incorporating low-power Bluetooth enables smaller, lower-cost designs with longer battery life. As a result, BLE has become commonplace for devices in many different industries, including healthcare, fitness, entertainment and manufacturing.
Many consumer portable electronic devices are incorporating BLE as a communication protocol to either augment or replace Bluetooth BR/EDR. BLE has an independent specification and is functionally incompatible with BR/EDR communication, however, the two protocols can coexist on a single device and even use the same radio for the physical signaling. This configuration is known as dual-mode Bluetooth. One common application of dual-mode Bluetooth is in wireless audio, where the high-throughput audio streams (think streaming music or a phone call) are transmitted over BR/EDR, while other communication data (device controls or app-specific data) use BLE.
What are the Security Concerns with Bluetooth LE?
One major difference between BLE and BR/EDR is that BLE devices are constantly “advertising” their presence through repeated transmissions of device information. This is how BLE devices announce themselves to other BLE devices within communication range. The BLE advertisement data may contain information about the device type, manufacturer and capabilities, among other details. Scanning devices use the BLE advertisements to determine if they should connect to the advertising device.
An important part of the BLE advertisement is the advertising address. This allows recipients of the advertisement to know the identity of the device where the advertisement originated and to connect to the advertising device if desired. This address is a unique identifier that, in its simplest form, is represented by the MAC address, a 6-byte value of the same format used by Ethernet networking. The continuous broadcasting of the advertisement address presents a potential security vulnerability in that the static MAC address could potentially be used in coordination with the signal strength of the advertisement to track the location of a specific device and thus the device owner. This is known as identity tracking (Figure 1).
Figure 1: Bluetooth Low Energy device tracking through static MAC address advertising.
How can Randomized Addresses Secure Bluetooth Devices?
The BLE specification provides a protection mechanism against such identity tracking by allowing for a Resolvable Random Private Address (sometimes called RPA or RRA) to be used as the advertisement address in place of a fixed MAC address (Figure 2). The randomized address can then be updated at semi-random intervals to defeat location tracking from a snooping agent. Each device can implement its own randomized address refresh design, but the interval is typically quasi-periodic (to prevent detection through the discovery of a constant periodic address change) and on the order of minutes.
The data payload of a BLE advertisement is not unique to a singular device and therefore is difficult to use for identity tracking. However, it has been shown under certain circumstances that portions of this data can be used for tracking in spite of an RPA. For this reason, it’s important to make good BLE product design choices when implementing advertising content and refresh intervals.
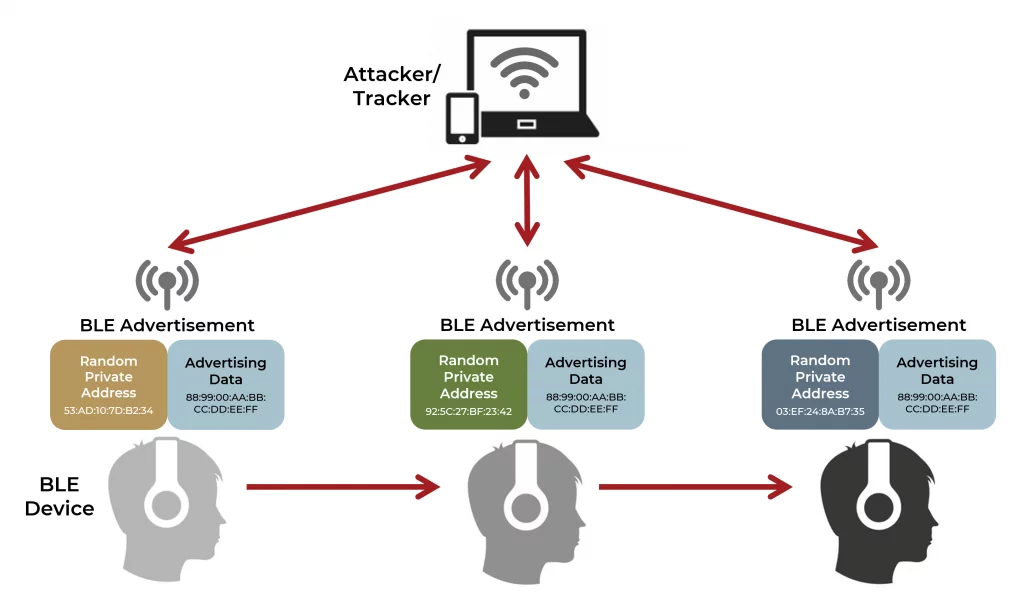
Figure 2: BLE device tracking protection using a Random Private Address.
Designing BLE Products to Use Randomized Addresses and Still Maintain Connectivity to Trusted Devices?
If a device is constantly changing the advertisement address in its BLE advertisements, how can devices that were previously connected detect and confirm the identity of the advertising device to resume secure communication? The answer is by securely pairing and bonding with each other. First, BLE devices create a secure pairing by discovering each other’s security levels and capabilities. This leads to the establishment of temporary encryption keys for the exchange of a long-term key (LTK) that the devices can use for encryption of exchanged data (Figure 3).
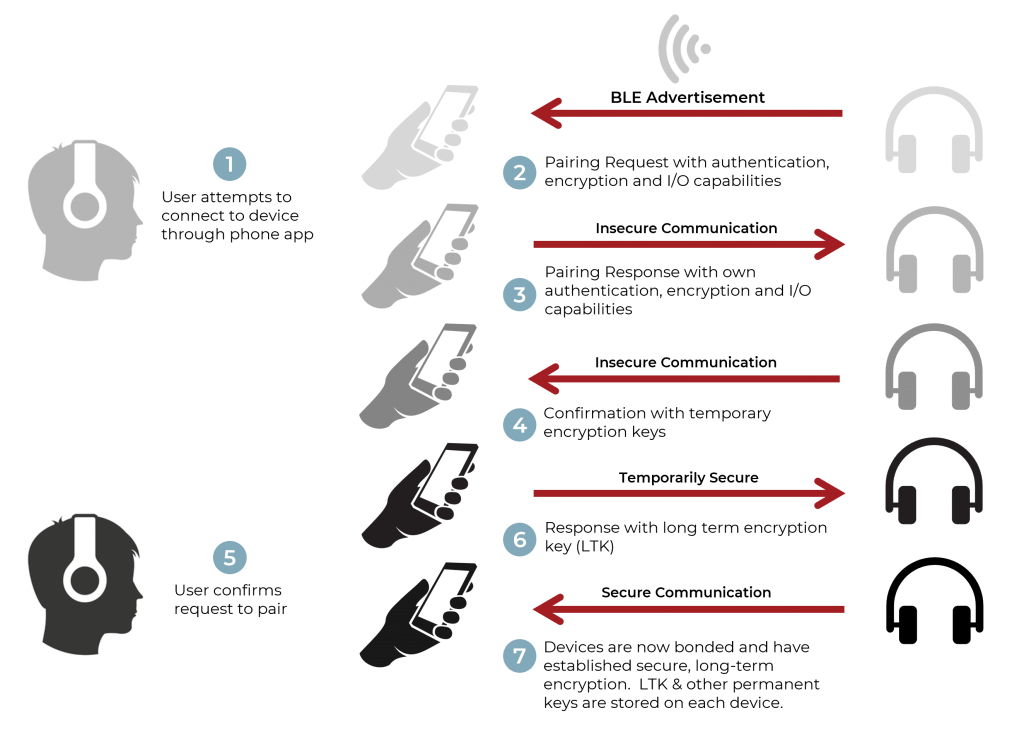
Figure 3: Establishing a secure Bluetooth Low Energy connection through the bonding process. This provides lasting encryption through the exchange of a long-term key (LTK).
The exchange and storage of keys between BLE devices is known as bonding. In addition to the LTK, the devices also exchange an identity resolving key (IRK). The IRK is used in conjunction with the Random Private Address to authenticate a connection when the randomized address changes periodically or a BLE device comes back within range (Figure 4). This allows known devices to remain connected to each other through randomized address changes but prevents untrusted devices from tracking your device through a fixed address.
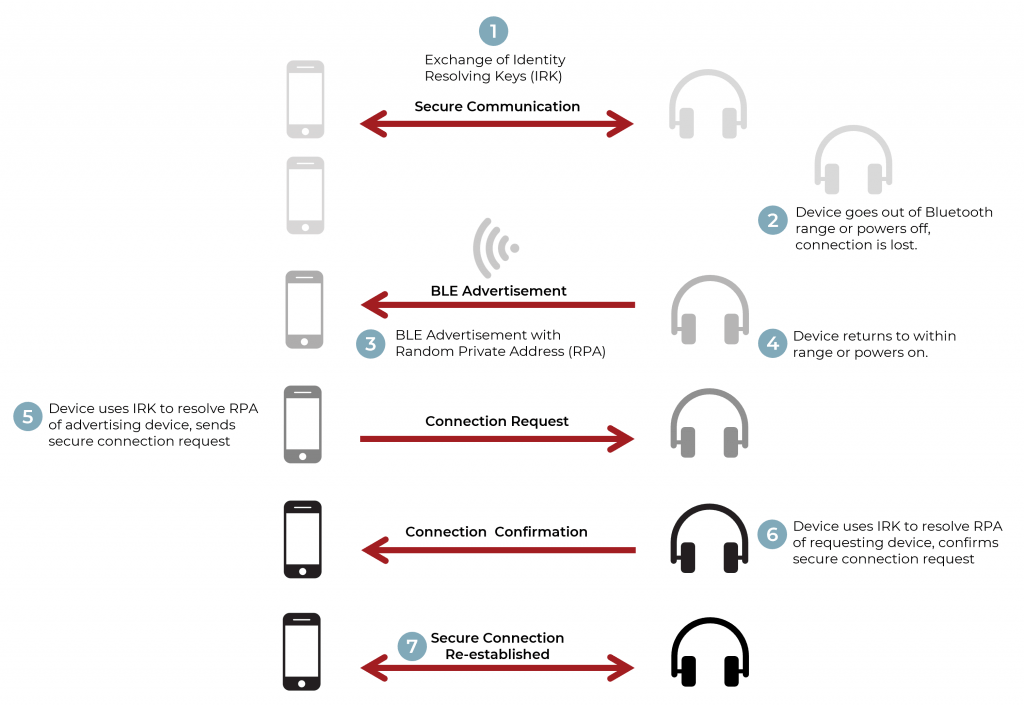
Figure 4: Establishing Bluetooth Low Energy privacy through the exchange and storage of an identity resolving key (IRK). The IRK is used to authenticate the devices upon resumption of a BLE connection.
The advertising address in a BLE advertisement is a 6-byte (48-bit) field, the same length as a device MAC address. Instead of transmitting a static MAC address, a device using an RPA will transmit a 22-bit random number (prand) and a 24-bit hash value, along with two fixed bits (Figure 5). To confirm a known device’s identity, the recipient of a BLE advertisement using an RPA will run a known encryption function on the 24-bit prand (using the 2 fixed bits) padded to 128 bits and the 128-bit IRK. If the result of the encryption function (truncated to 24 bits) matches the 24-bit hash value extracted from the address field of the advertisement, the address has been resolved and the device’s identity confirmed. The two devices can then continue to communicate in a secured and private manner.
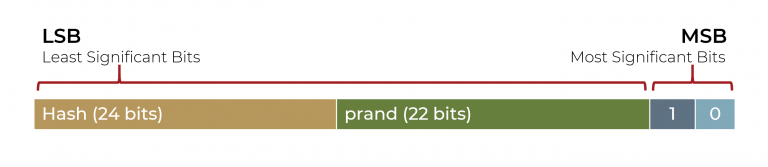
Figure 5: Using a Resolvable Private Address in BLE advertisement.
Bluetooth Low Energy devices have become widespread in popularity due to their low power requirements, which enable smaller, lower-cost designs. The use of dynamic, random resolvable addresses in place of static addresses in BLE advertising provides protection from unwanted identity tracking, yet allows trusted devices to maintain secure communication. This feature provides peace of mind for users of BLE-enabled wireless devices all across the world.
Learn more about Bluetooth LE and IoT testing on our page Zigbee, Matter, Thread & Bluetooth Mesh IoT Testing Services.
